Hallo Admin,
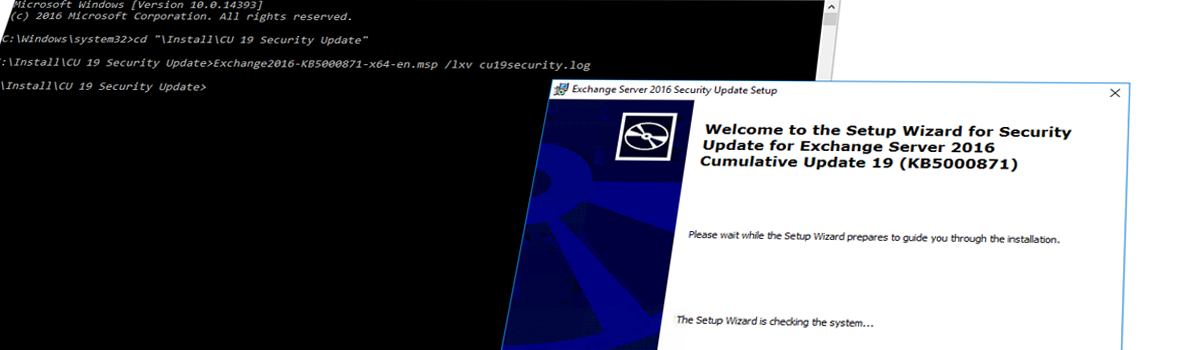
es gibt neue Sicherheitsupdates für Exchange Server: Dieses mal für alle Versionen von Exchange Server 2010 bis Exchange Server 2019:
- Exchange Server 2010 (RU 31 for Service Pack 3 – this is a Defense in Depth update)
- Exchange Server 2013 (CU 23)
- Exchange Server 2016 (CU 19, CU 18)
- Exchange Server 2019 (CU 8, CU 7)
Die hier aufgezeigte 0-Day wird wohl bereits aktiv ausgenutzt. Microsoft empfiehlt allen Kunden umgehend zu Patchen!
Laut Microsoft wird die Sicherheitslücke mit dem CU20/CU9 für Exchaneg Server 2016/2019 im März geschlossen. Dies kann jedoch noch 3 Wochen auf sich warten lassen.
Mit den folgenden Codebeispielen von Microsoft kann herausgefunden werden ob der eigene Server bereits „angegriffen wurde“:
CVE-2021-26855 exploitation can be detected via the following Exchange HttpProxy logs:
- These logs are located in the following directory: %PROGRAMFILES%\Microsoft\Exchange Server\V15\Logging\HttpProxy
- Exploitation can be identified by searching for log entries where the AuthenticatedUser is empty and the AnchorMailbox contains the pattern of ServerInfo~*/*
- Here is an example PowerShell command to find these log entries:
Import-Csv -Path (Get-ChildItem -Recurse -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy” -Filter ‘*.log’).FullName | Where-Object { $_.AuthenticatedUser -eq ” -and $_.AnchorMailbox -like ‘ServerInfo~*/*’ } | select DateTime, AnchorMailbox
- If activity is detected, the logs specific to the application specified in the AnchorMailbox path can be used to help determine what actions were taken.
- These logs are located in the %PROGRAMFILES%\Microsoft\Exchange Server\V15\Logging directory.
CVE-2021-26858 exploitation can be detected via the Exchange log files:
- C:\Program Files\Microsoft\Exchange Server\V15\Logging\OABGeneratorLog
- Files should only be downloaded to the %PROGRAMFILES%\Microsoft\Exchange Server\V15\ClientAccess\OAB\Temp directory
- In case of exploitation, files are downloaded to other directories (UNC or local paths)
- Windows command to search for potential exploitation:
findstr /snip /c:”Download failed and temporary file” “%PROGRAMFILES%\Microsoft\Exchange Server\V15\Logging\OABGeneratorLog\*.log”CVE-2021-26857 exploitation can be detected via the Windows Application event logs
- Exploitation of this deserialization bug will create Application events with the following properties:
- Source: MSExchange Unified Messaging
- EntryType: Error
- Event Message Contains: System.InvalidCastException
- Following is PowerShell command to query the Application Event Log for these log entries:
Get-EventLog -LogName Application -Source “MSExchange Unified Messaging” -EntryType Error | Where-Object { $_.Message -like “*System.InvalidCastException*” }CVE-2021-27065 exploitation can be detected via the following Exchange log files:
- C:\Program Files\Microsoft\Exchange Server\V15\Logging\ECP\Server
All Set-<AppName>VirtualDirectory properties should never contain script. InternalUrl and ExternalUrl should only be valid Uris.
- Following is a PowerShell command to search for potential exploitation:
Select-String -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\ECP\Server\*.log” -Pattern ‘Set-.+VirtualDirectory’
Zudem findet man hier noch einige weitergehenden Informationen:
- Microsoft Security Response Center (MSRC) blog.
- HAFNIUM Targeting Exchange Servers
- Defending Exchange servers under attack
- Hafnium: Sicherheitsupdates jetzt installieren | Microsoft News
Happy Updating
Andi



Hinterlasse einen Kommentar